Chasing Cyber - #22 - Quantum Keys
NATO looks forward, GCHQ looks back, BSI looks around
Welcome to the 22nd edition! This week we focus on quantum key distribution and Hollywood B-listers.
An Allied Approach to QKD
NATO just announced its Quantum Technologies Strategy.
Their stance on quantum key distribution is more positive than we see from individual governments. Here’s what they say:
“In the future, further improvements could allow quantum key distribution to also contribute to secure communications.
... Allies can support each other... in the development and implementation of post-quantum cryptography and quantum key distribution to enhance the quantum-resilience of our networks.”
It’s great to see a balanced statement on the topic from NATO. To date, I’ve found national governments unnecessarily critical of QKD. At a conference last year, the French ANSSI even described it as “science fiction”.
QKD isn’t ready for large-scale deployment yet. But there’s no need to pour cold water on a technology that may offer future security improvements for critical communications. Well done to NATO for treating it fairly.
I also thought the conclusion of their quantum threat section was particularly interesting:
“Strategic competitors and potential adversaries may also leverage disinformation opportunities within Allied societies by creating public distrust of the military use of quantum technologies. Allies will seek to prevent and counter any such efforts through the use of strategic communications. NATO will support Allies as required.”
You can read the summary document here.
A History Lesson from GCHQ (and Hollywood)
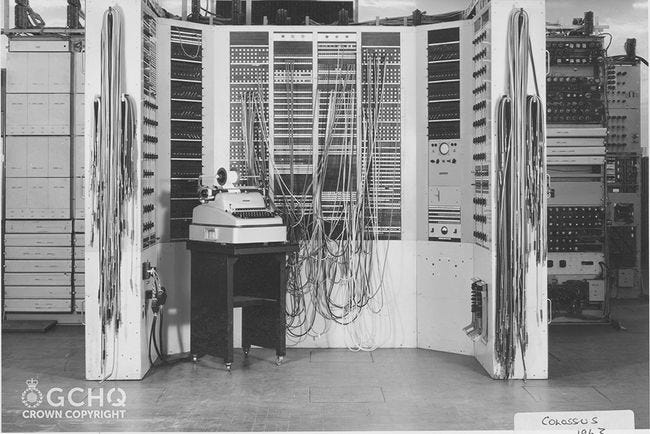
Colossus was the Stephen Baldwin of World War II.
Despite being a strong contributor to the Allied success, few people know about Colossus. Pop culture favours the Enigma-busting Bombe machine instead.
To help rebalance this, GCHQ is celebrating the 80th anniversary of the Colossus machine, with some never-before-seen images:
Colossus was used to crack the Lorenz cipher, which encrypted strategic messages between senior German officers. It is widely regarded as the first programmable digital computer system.
The Colossus was kept secret until the early 2000s, which might explain its lack of fame. By contrast, the world learned the Enigma storyline back in the 1970s.
These stories make me wonder whether present-day ciphers have been similarly broken. I guess we’ll need to wait 30 years to find out.
You can read the GCHQ article here. And you can learn more about Colussus on Wikipedia.
QKD under das Mikroskop
If you’re building or buying a QKD system, you need to read this document.
The industrious folks at the German BSI have compiled the most comprehensive survey of QKD implementation attacks I’ve ever seen.
Over 300 papers were analysed, and 49 attack paths were identified. Each attack is graded with a feasibility score, and known countermeasures are listed.
One conclusion from the document is more research into continuous-variable (CV-QKD) systems is needed. The older and more established discrete-variable (DV-QKD) protocols have seen far more scrutiny over the years. This is reflected in the number of papers and attacks found so far.
The document is mostly news for QDK nerds. However, the opening sections provide a good overview of QKD technology, which would benefit the general reader.
You can access the report on the BSI website.