Chasing Cyber - #27 - Zeitgeist
Apple, RSA keys, and Daniel Bernstein
This week, we’re returning to a blend of quantum cyber news and straight-up cryptography. Thank you to JJ for helping me steer the course of this newsletter! Let’s dive into the contents.
Apple Makes Post-Quantum Cool
Everyone’s talking about Apple's PQ3 announcement, but most reports miss the point. The important thing is NOT the technology.
The real significance of Apple adding post-quantum security to iMessage is the impact on the zeitgeist.
In the UK, the BBC’s prime-time radio show dedicated three minutes to the topic. Ten million listeners learned about post-quantum security while cooking their bangers and mash.
Outlets like Bloomberg and Fast Company also reported on the news, driving awareness into executive minds across the world. I suspect opinion pieces will soon appear in other major outlets as their editors notice the splash Apple’s announcement has made.
This is coverage of post-quantum security at a scale we’ve never seen before.
A raft of similar high-profile announcements will no doubt follow, as organisations race to be seen as security thought leaders. We’ve already seen this on a smaller scale in the last year, with Signal, OpenSSL and Google making their first announcements.
2024 has started with a bang for PQC, and Apple has done the industry a huge favour by raising awareness to new heights. I’m excited to see what happens next as we steam towards NIST's publication of the final standards.
If you haven’t seen the Apple blog yet, check it out here.
RSA Key Fingerprinting
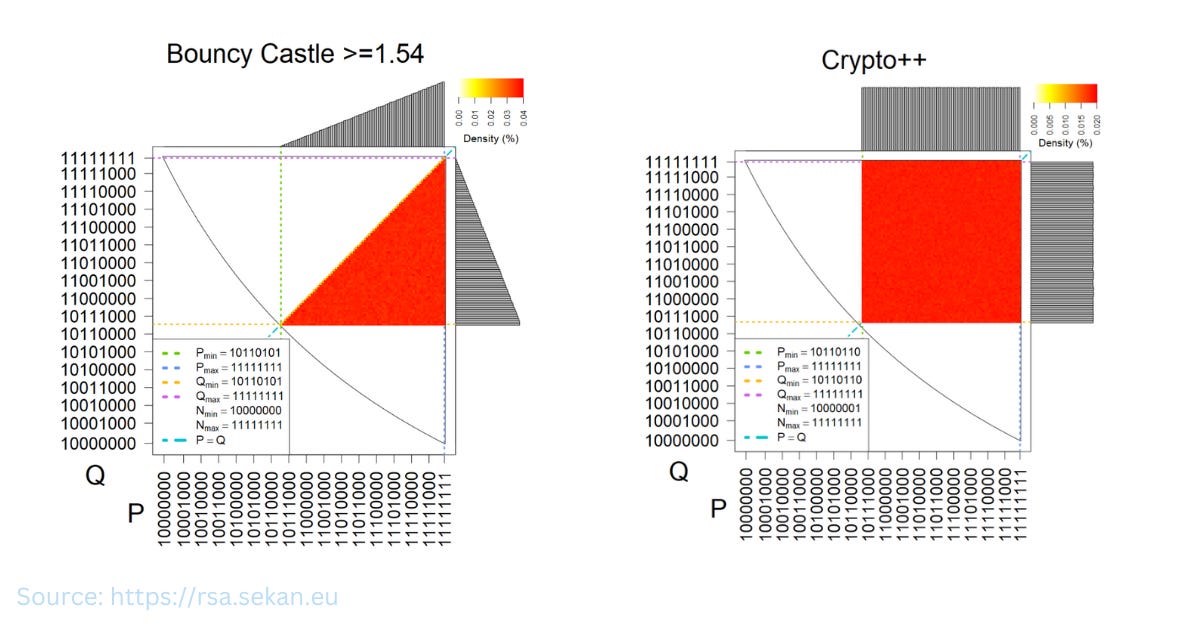
Did you know RSA public keys have fingerprints that identify the cryptographic library that generated them?
In a paper from 2016, researchers studied sixty million keys generated by a range of open-source libraries and closed-source smartcards. By analysing the most significant byte of the public key modulus, distinct patterns were found.
These “fingerprints” can be used to identify which library generated a given key. The underlying patterns are caused by different approaches to the difficult task of prime number generation. The paper authors created heat maps, showing the likely distribution of bits, which are quite fascinating.
These fingerprints are not just a curiosity – they represent a potential cyber risk. If a vulnerability is discovered in a popular library, these fingerprints could be used to identify vulnerable keys in the wild. Similarly, fingerprinting could aid deanonymisation when using services like Tor.
You can see more of these cool graphs, and find links to the paper, on this website: https://rsa.sekan.eu/. And a hat-tip to my colleague Kevin Milner for drawing my attention to this paper several months ago.
Hybrid Opinions
Most post-quantum implementations, including Apple's PQ3, rely on a hybrid of traditional and PQC algorithms. So why are governments in the US and the UK still lukewarm on this concept?
In January, Daniel Bernstein posted an interesting blog with his views. It’s worth reading if you're building a quantum-safe system and are debating whether to go hybrid or not.
For those new to Bernstein's writing: brace yourself for conspiracy-theory vibes and plentiful jabs at NIST, the NSA, and allied organisations (like GCHQ). Yet, there is wisdom in what he writes. He carefully dissects the arguments against using hybrid modes and finds them wanting.
Check out his blog post here.